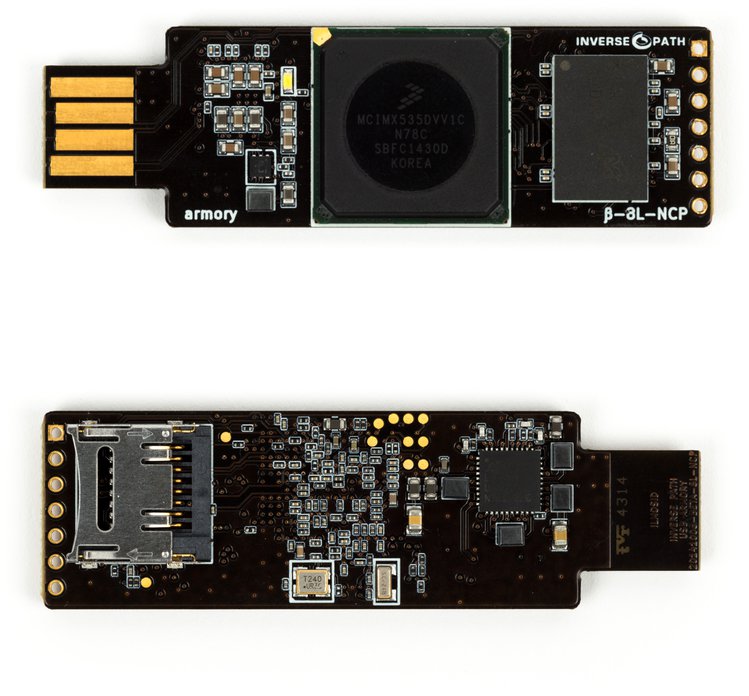
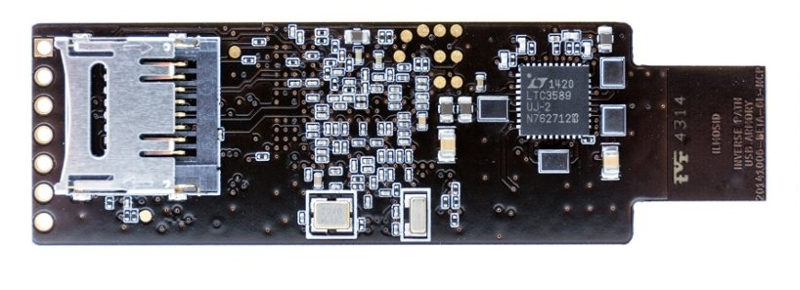
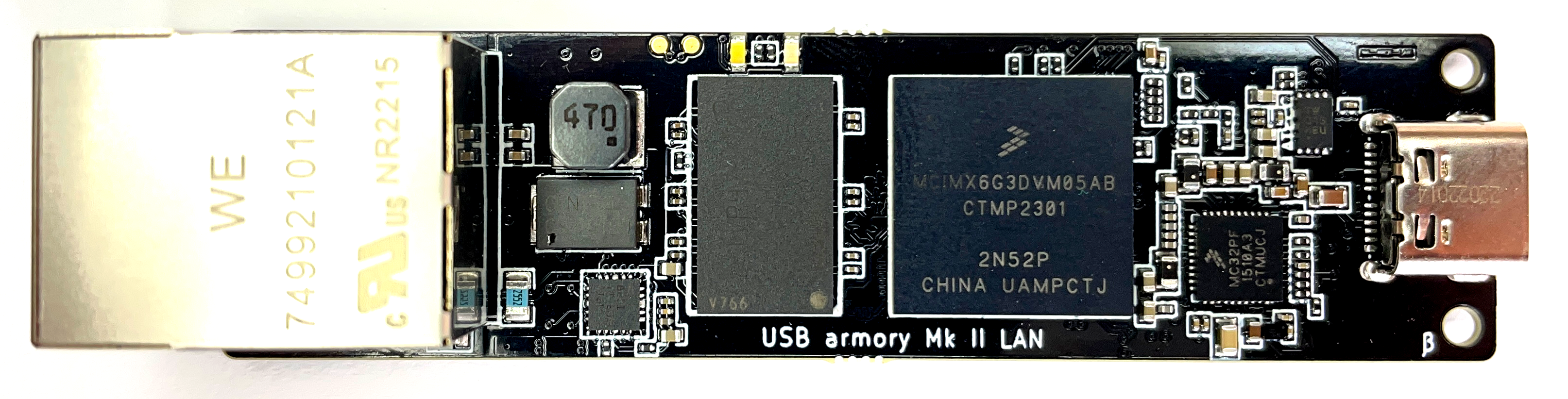
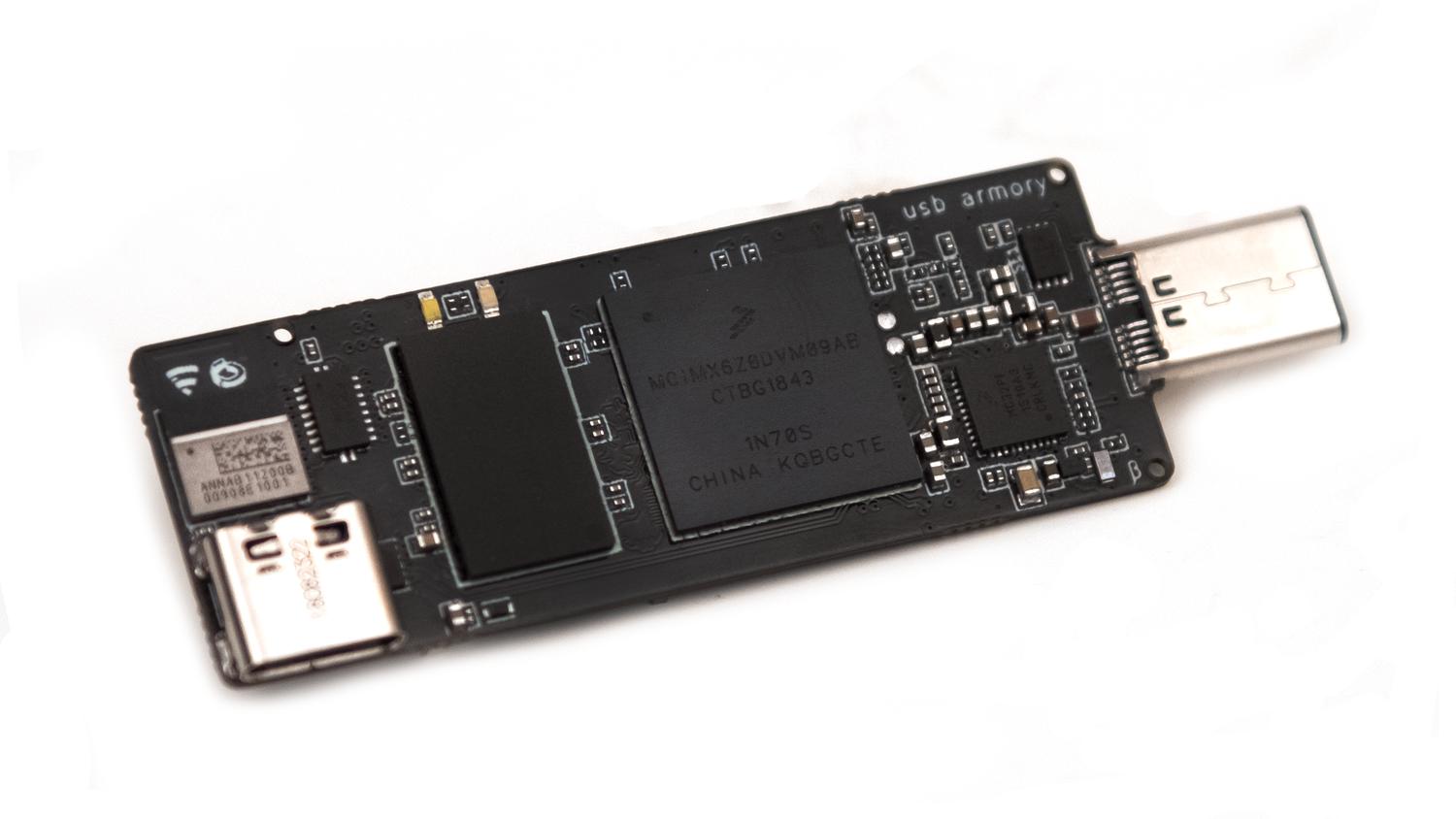
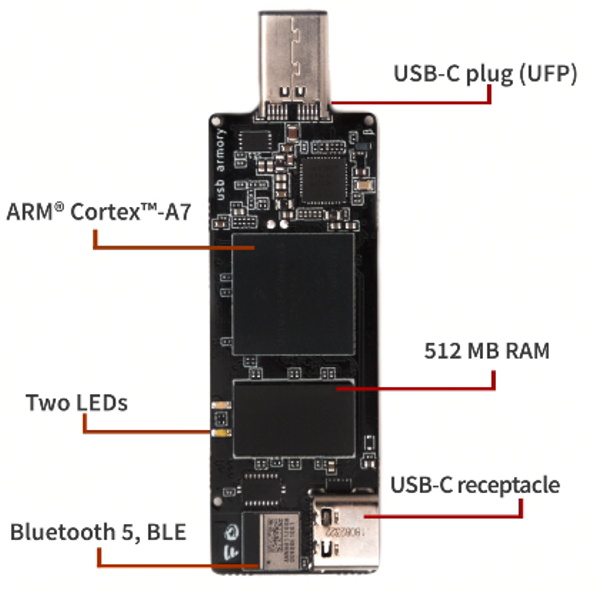
WithSecure™ on X: "NEWS: F-Secure's USB armory Mk II packs industrial-grade security into a computer the size of a thumb https://t.co/97r75u7bfk" / X

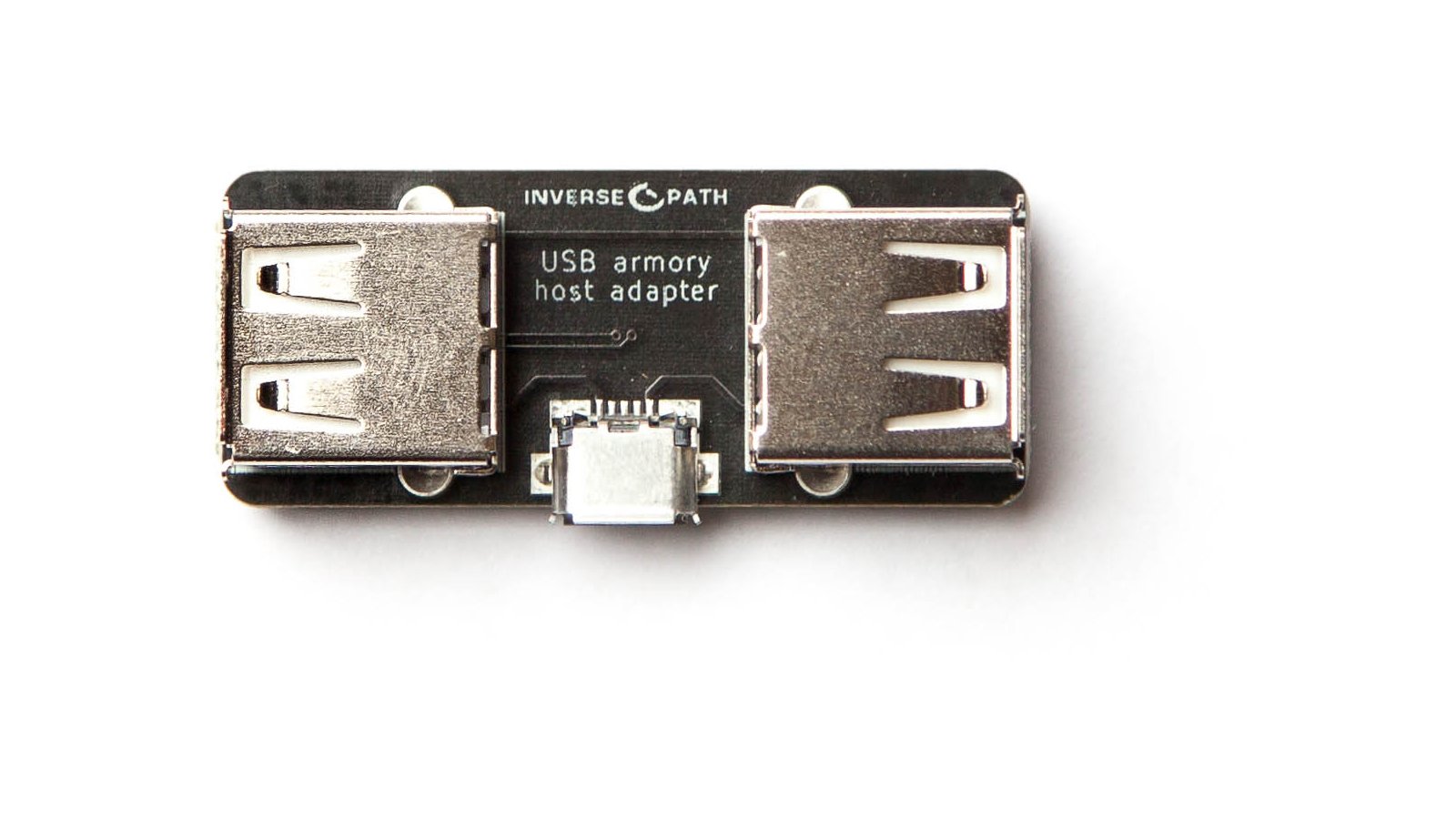
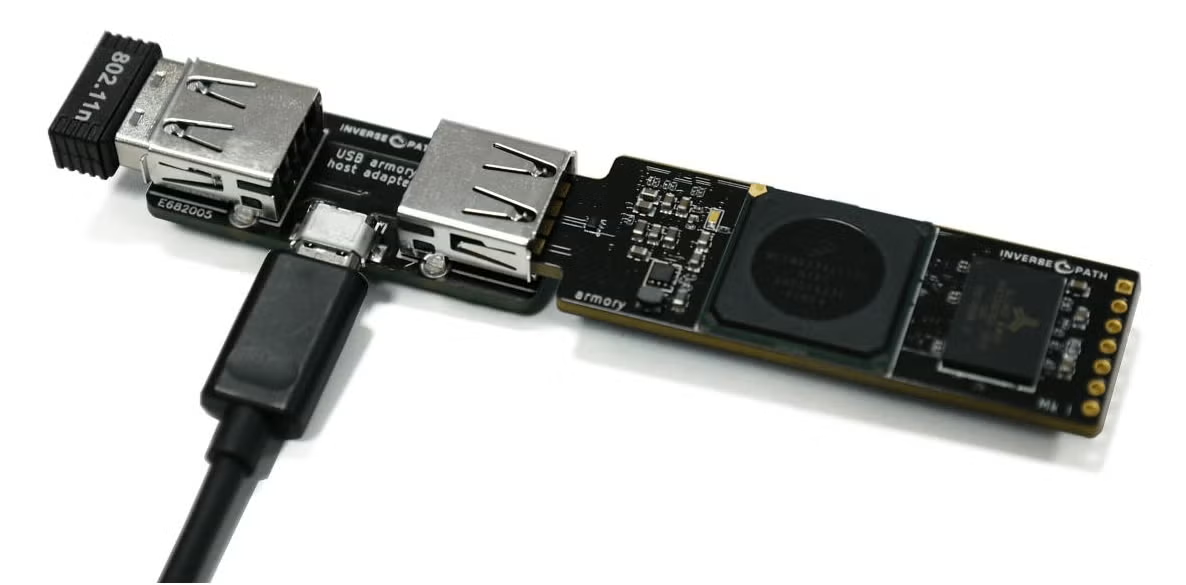
Open Source Hardware Design Developing And Running A Variety Of Applications Usb Armory Kit Host Adapter Enclosure - Integrated Circuits - AliExpress